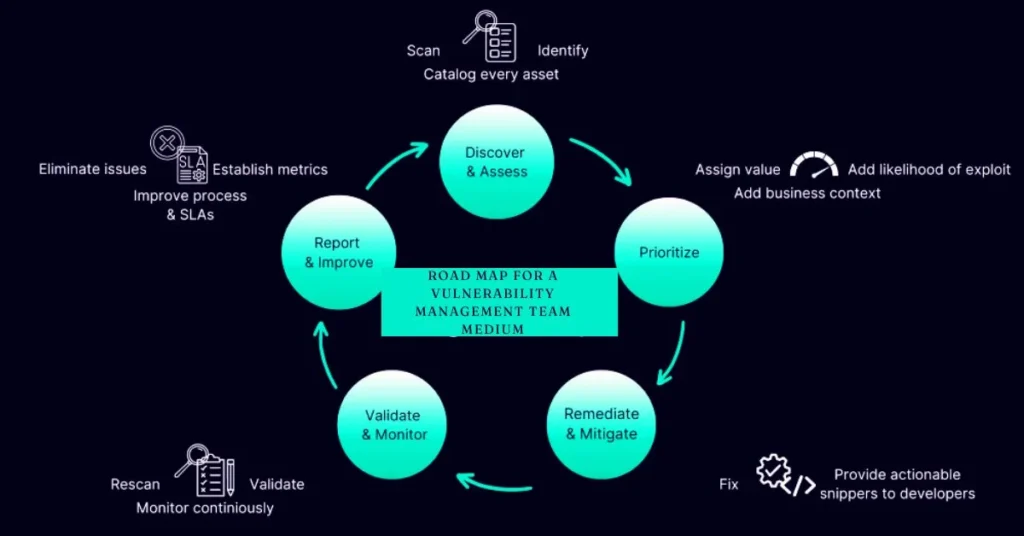
Introduction to road map for a vulnerability management team medium
In today’s digital landscape, the importance of a robust vulnerability management strategy cannot be overstated. Cyber threats are evolving at an alarming rate, and organizations must stay ahead to safeguard their assets. Enter the road map for a vulnerability management team medium—a structured approach designed to navigate the complexities of identifying and mitigating risks effectively.
Imagine having a dedicated team that not only spots vulnerabilities but also prioritizes them based on potential impact. This ensures resources are allocated wisely while fostering a culture of security within your organization. Whether you’re starting from scratch or looking to enhance an existing framework, understanding how to build and maintain this team is essential.
Let’s dive into what makes up an effective vulnerability management team and explore the path toward creating one that can withstand modern cyber challenges.
ALSO READ: Is Medium a Good Platform for Extracurricular Activities? Find Out
Benefits of a Vulnerability Management Team
A well-structured Vulnerability Management Team brings numerous advantages to an organization. First, it enhances security posture by proactively identifying and addressing weaknesses before they can be exploited.
This team fosters a culture of continuous improvement. Regular assessments lead to updated strategies that adapt to emerging threats.
Additionally, having a dedicated group streamlines communication across departments. They serve as the central point for vulnerability reporting and resolution, ensuring everyone is on the same page.
Cost efficiency is another significant benefit. By mitigating risks early, organizations save money that might otherwise go towards responding to breaches or incidents.
A strong vulnerability management initiative also boosts compliance with regulations and industry standards. This not only protects data but builds trust with clients and stakeholders who value security practices.
Key Players in a Vulnerability Management Team
A successful vulnerability management team thrives on collaboration. Key players each bring unique skills to the table.
First, there’s the Vulnerability Analyst. This individual identifies and assesses potential security threats. Their expertise is crucial for prioritizing vulnerabilities based on risk.
Next up are Security Engineers, who focus on remediation efforts. They implement fixes and work closely with other IT teams to ensure systems remain secure.
The Compliance Officer plays a pivotal role too. Ensuring that all actions adhere to industry regulations keeps organizations out of legal trouble.
Communication is essential as well. The Project Manager coordinates tasks, timelines, and resources, ensuring everyone stays aligned during vulnerability assessments.
Involving stakeholders from various departments—such as IT support or application development—fosters a culture of security awareness throughout the organization. Each player contributes significantly to building a resilient defense against cyber threats.
Steps to Building an Effective Vulnerability Management Team
Building an effective vulnerability management team begins with defining clear roles. Identify key positions, such as a team leader, security analysts, and incident response members. Each role should have distinct responsibilities focused on specific aspects of vulnerability management.
Next, establish communication protocols. Open lines of communication facilitate quick information sharing among team members and other departments. Regular meetings ensure everyone is aligned on priorities and ongoing tasks.
Training is essential for maintaining a knowledgeable team. Provide resources to keep skills sharp and awareness up-to-date regarding new vulnerabilities and threats.
Implement processes for vulnerability assessment and prioritization. This gives the team a structured approach to tackle issues based on risk levels.
Foster a culture of collaboration within the organization. Engage stakeholders from different departments for broader insights that can enhance your team’s effectiveness in managing vulnerabilities.
Tools and Technologies for Vulnerability Management
When it comes to vulnerability management, the right tools can make all the difference. These technologies help teams identify, prioritize, and remediate vulnerabilities efficiently.
Scanning tools are essential. They automate detection processes across systems and applications. Popular options include Nessus and Qualys, which provide comprehensive assessments.
For effective tracking, consider using a vulnerability database like CVE or NVD. This ensures your team stays updated on known threats and vulnerabilities with ease.
Integration is key as well. Solutions that work seamlessly with existing security information and event management (SIEM) systems enhance visibility. Tools like Splunk or IBM QRadar can consolidate data for better analysis.
Don’t overlook collaboration platforms for communication among team members. Tools such as Jira or Trello foster teamwork while managing tasks effectively within the vulnerability lifecycle.
Best Practices for Managing Vulnerabilities
Managing vulnerabilities effectively requires a proactive approach. Regularly scan systems and applications to identify potential weaknesses before they can be exploited.
Prioritize findings based on risk levels. Focus on critical vulnerabilities that pose the highest threat to your organization first. This ensures resources are allocated efficiently.
Incorporate continuous training for your team. Keeping up with emerging threats and new technologies is essential in staying ahead of cybercriminals.
Implement a robust patch management process. Timely updates reduce the window of opportunity for attackers significantly.
Document everything, from vulnerability assessments to remediation actions. A well-maintained record helps track progress over time and supports compliance efforts.
Foster collaboration across departments. Engaging different teams—IT, security, and development—creates a unified front against risks while enhancing overall awareness of vulnerability management practices.
Challenges and Solutions for a Successful Vulnerability Management Team
Building a successful vulnerability management team comes with its share of hurdles. One common challenge is the overwhelming volume of vulnerabilities reported daily. Teams can easily become bogged down, losing track of critical issues.
Another obstacle lies in coordination among departments. Differences in priorities and communication gaps can hinder effective responses to threats. Encouraging collaboration through regular meetings can bridge this divide.
Resource allocation remains a persistent issue as well. Many teams struggle with insufficient manpower or tools to address all identified vulnerabilities efficiently. Fostering partnerships with third-party vendors might offer additional support and resources.
Keeping up-to-date with evolving cyber threats is essential but challenging. Continuous training and adopting new technologies can empower team members to stay ahead in the game while enhancing their skills for better performance on the front lines against potential risks.
Conclusion
A successful vulnerability management team requires a combination of skilled individuals, effective processes, and the right tools. By addressing common challenges and implementing solutions such as regular collaboration, resource allocation strategies, and continuous training, teams can overcome obstacles and become stronger in their efforts to protect their organization’s assets.
It is also important for teams to regularly review and update their processes to adapt to evolving threats. This includes continuously monitoring for new vulnerabilities, prioritizing them based on risk assessment, and promptly addressing critical issues.
Furthermore, open communication and a strong partnership with other departments within the organization are crucial for a successful vulnerability management team. This will ensure that all stakeholders are on the same page when it comes to identifying and addressing vulnerabilities.
Overall, building a successful vulnerability management team takes time, effort, and continuous improvement. However, by addressing challenges head-on and implementing effective solutions, teams can play a critical role in safeguarding their organization’s data and systems from potential cyber threats.
ALSO READ: Does Medium Publish Literature Reviews? A Comprehensive Guide
FAQs
1. What is a “road map for a vulnerability management team medium”?
A road map for a vulnerability management team medium is a structured approach that helps guide the team in identifying, prioritizing, and remediating security vulnerabilities within an organization. It provides direction, allocates resources efficiently, and fosters collaboration to enhance overall cybersecurity resilience.
2. How do you build an effective vulnerability management team?
Building an effective team involves defining clear roles, establishing communication protocols, and providing ongoing training. Additionally, setting up structured processes for vulnerability assessment and fostering collaboration with other departments are key to a team’s success.
3. What tools are essential for vulnerability management?
Essential tools include automated scanning solutions like Nessus and Qualys, vulnerability databases such as CVE or NVD, and integration with SIEM systems like Splunk. Collaboration platforms like Jira or Trello also help streamline communication within the team.
4. What are the benefits of having a vulnerability management team?
A dedicated vulnerability management team improves security posture, reduces costs by preventing breaches, ensures compliance with regulations, and fosters a culture of continuous improvement within the organization.
5. How do you prioritize vulnerabilities effectively?
Vulnerabilities should be prioritized based on their potential impact on the organization. Focus on critical vulnerabilities first, and ensure that resources are allocated wisely to mitigate the highest risks before they escalate. Regular assessments and updates help maintain this prioritization.